Do you know your data has been leaked? Your customer information, intellectual property right information, financial data and individual file are facing the risk of leakage. However, the one causes such result is not definitely the hacker but may be your own employee. Whether unintentionally or maliciously, email, online information release, flash disk or printing may leak the data.
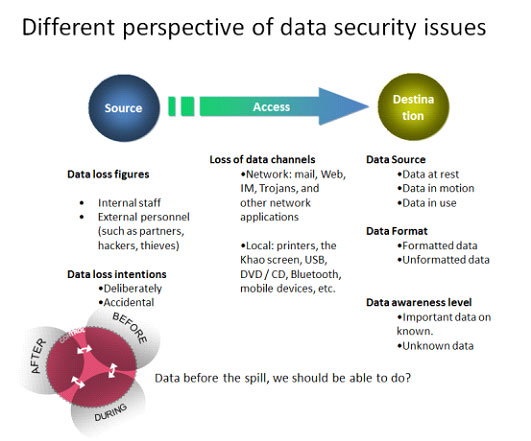
To prevent the huge loss caused by data leakage, Rich Cloud Technology relies on Data Loss Prevention (DLP) solution to comprehensively monitor the transmission of the most important data. No matter under which circumstance (working, home or on the way), it may conduct real-time monitoring of the data to effectively prevent the confidential data from losing. DLP may prevent the enterprise from many risks: economic loss, brand damage, customer loss, competition frustration and violation.
Architecture of DLP comprehensive solution
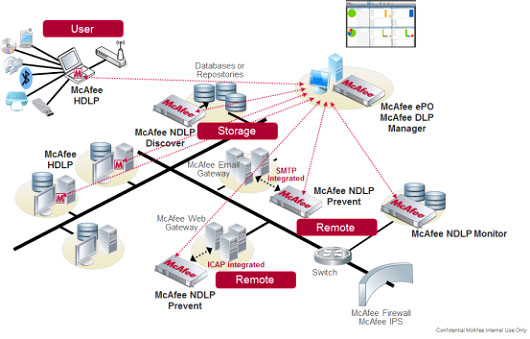
DLP comprehensive solution mainly consists of following aspects:
Network data leakage prevention
Terminal data leakage prevention
Database layer leakage prevention
File life cycle management
Mobile terminal data leakage prevention
Comprehensive management
DLP may fulfill following demands:
Data loss protection may prevent data leakage in ways of mail sending, website browsing, unauthorized printing, USB copying and screen snapping software.
It may timely control the loss of various sensitive data and provides 4 optional operations
Evidence collection
Real-time blocking
Informing user and administrator
Sensitive data isolation
Complete control of data and equipment
Only the device authorized by the company may be used within the range of the company
Data is only allowed to be copied to the device authorized by the company.
It realize the device blocking function and may distribute the strategy according to the manufacturer identification, device identification and serial number of the plug-and-play device
User group and department configures the use strategy of the plug-and-play device for different users
It records the log and audits the behavior of the user and device use.
A set of portable secure storage device
Strong visiting control function and encryption guarantees the security
It protects the security of the sensitive data transmission process
Centralized administration is easy for implementation
The product support various devices such as laptop, office computer and mobile device
Detailed auditing record
It supports many strong authentication ways
Encryption algorithm passes the certification of FIPS 140-2, Common Criteria Level 4 (highest level of software product), BITS and CSIA
Case Study:
Online Banking Project for Banking Industry
Blade Server, Storage, Network and Virtualization Construction of Large Manufacturing Enterprise
