Along with the rapid development of computer technology and communication technology, network is gradually changing the work and life style and becoming a theme of the current social development. Enlarged openness, interconnectivity and sharing, especially the appearance of Internet make the network more important and influential to the society. Along with the prosperity of emerging services such as e-commerce, e-cash, digital currency and online bank, network security becomes more and more important.
Economic loss caused by the computer network crime is also astonishing. Direct economic loss in the US only reaches USD 15 billion every year. There is an online intrusion event every twenty seconds in the world. Nearly 80% companies are intruded online at least once a week, and all users may be involved once the hacker discovers the weak point of the system. Forceful measures must be taken to guarantee the security of the computer network.
Besides, as the network scale is enlarged and the complexity is increased, guarantee of the information security becomes more strict. In fact, network and information security is a long-term comprehensive systematic engineering existing in the whole information era.
Network security architecture mainly consists of following parts:
Rich Cloud Technology strictly follows following principles when providing the user with the network architecture design and planning:
1.Integrity and wholeness principle:Ideas and methods of the system engineering shall be used to analyze the security and specified measures of the network. Security measures mainly include: administrative and legal method, various administration systems (personnel investigation, work flow, maintenance and security system) and professional measures (identification technology, storage and access control, password, low radiation, fault tolerance, virus prevention and highly secure product). A favorable security measure is generally the result of the proper and comprehensive application of many methods. In a computer network including individual, device, software and data, effective and feasible measures can only be obtained by viewing and analyzing the position and influence of these parts from the systematic perspective, that is, the computer network security shall obey the comprehensive security principle to establish the reasonable network security system architecture according to the specified security strategy.
2. Demand, risk and cost balance principle:
It is difficult and unnecessary to realize the absolute security in any network. It shall practically research a network (including task, performance, architecture, reliability and maintainability), qualitatively and quantitatively analyze the threat and potential risk of the network and regulate specifications and measures to determine the security strategy of this system.
3. Conformity principle:
Conformity principle refers to that the network security problem shall exist simultaneously with the service cycle (or life cycle of the whole network), and the regulated security system architecture must be consistent with the security demand of the network. As for the secure network system design (including preliminary or detailed design) and implementation plan, network verification, acceptance and operation, it is better to consider security measures in the initial period than after the completion of the network construction since it is easier and costs less.
4. Operability principle:
Security measures shall be completed by the person, so if the measure is too complicated to operate, the security itself is reduced. Besides, adoption of the measure shall not influence the normal operation of the system.
5. Principle of implementation by steps:
Since the expansion scope of the network system and its application is broad, as the network scale expands and the application increases, the network vulnerability will continues to increase and it is unpractical to solve the network security problem once and for all. Besides, since it cost much to implement the information security measure, implementation by steps may fulfill the fundamental demand of the network system and information security and save the cost.
6. Multiple protection principle:
No security measure is absolutely secure against the attack. However, if a multiple protection system is established, various layers of protection mutually supplement and once a layer of protection is breached, other layers of protection may still protect the information security.
7. Principle of assessable property:
Prior assessment of a security design and verification of the network security shall be conducted by the national network information security assessment and authentication institution.
Common architecture of the network security:
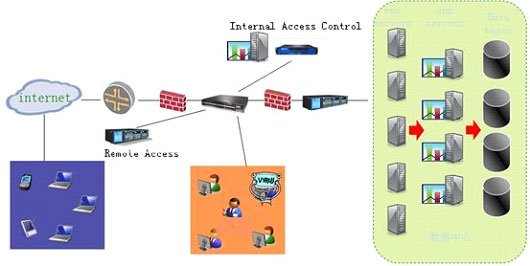
Case Study:
Voice and Video Project of a Third-Party Payment Company
Data Center Platform Construction for a Large Manufacturing Enterprise
